Leaked NSA tools, now infecting over 200,000 machines, will be weaponized for years
More than 200,000 machines have been infected by an NSA backdoor leaked nearly two weeks ago by the Shadow Brokers hacking group, according to the latest scans and estimates. Experts expect to see the exploits, implants and other NSA-built hacking tools in use for as long as a decade into the future.
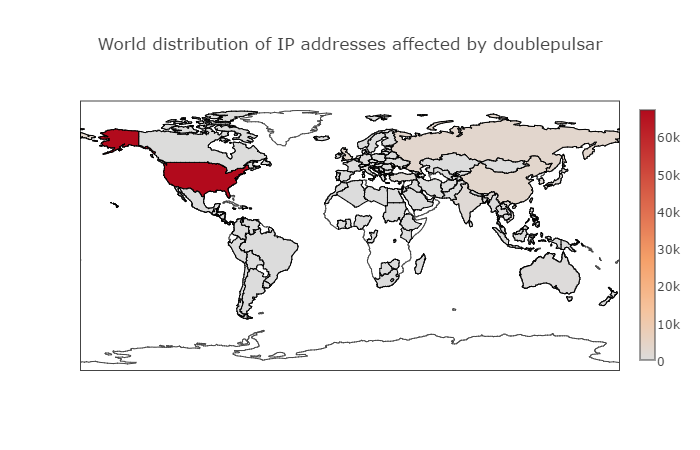
U.S. computers are by far the most frequently hit targets of DOUBLEPULSAR, a backdoor implant allowing attackers to stealthily collect information and run malicious code on a target’s machine, according to the Swiss security firm Binary Edge, which counted 183,107 infected machines as of early Monday morning. More than 67,000 of those machines were American, while China, Russia and the U.K. have suffered several thousand infections each. On Friday, that number was 100,000 globally. An average of 25,000 machines have been infected globally every day over the last week.
Experts say the actual number is higher than Monday’s assessment because each count is slow and does always not catch everything while the infection is a growing and moving target.
“I would estimate it is safe to say there are between 200,000 and 300,000 hosts on the internet infected with this,” Dan Tentler, CEO of the security firm Phobos Group told CyberScoop on Monday.
“The bloodbath will continue,” he said. “It’s going to get worse. The reason we’re in this mess is because the people who run these computers don’t care about computers and don’t patch their systems. The patch was available for this bug a month ago. The people who are currently infected didn’t patch.”
The impact, however, can extend far beyond the immediately infected victims. The new situation is comparable to the Mirai botnet, when a mountain of poor security practices left a ton of machines easily hackable and handed a highly effective weapon over the criminals. As a result, a huge swatch of the internet came crashing down.
Over the weekend, security researcher Kevin Beaumont set up a honeypot — a vulnerable machine meant to observe hacking — and saw it was infected within 15 minutes.
“The U.S. is the country that has the most IP addresses allocated to it, so if these implants are now being used by hackers in mass-scale compromises, it’s easy to understand why the U.S. would have more infections as it also has the biggest attack surface,” Binary Edge’s Tiago Henriques told CyberScoop.
DOUBLEPULSAR has been described as a “loading dock for extra malware.” It communicates over the Microsoft Server Message Block port, listens, receives instructions and executes attacks.
The number of infections should keep rising: Twenty percent of all machines vulnerable to DOUBLEPULSAR have been infected, according to Dan Tentler, CEO of the security firm Phobos Group. That leaves another 80 percent of infected machines waiting idly for an inevitable attack.
Groups of hackers around the world have co-opted the leaked NSA tools for their own ends. After an infection, attackers are then able to steal data, pivot into internal networks and attack other machines as well as to apply more persistent backdoors.
A different story illustrates why they’ll probably be able to use the leaked tools for awhile: The most exploited vulnerability in both 2015 and 2016 was the software flaw that allowed the famous Stuxnet virus to spread, as CyberScoop reported last week. It was discovered in 2010 and continues to have a widespread impact, largely because there are so many unpatched Windows machines.
Kaspersky Lab’s J.A. Guerro-Saade said on Monday he expects the leaked NSA tools to cause problems for more than five years.
Beaumont, reflecting on how “reliable and easy to use” the newly leaked tools are, expects them to be workable in the wild for the next decade.
These are “core Windows issues, shipped with [the operating system], remotely exploitable, unauthenticated,” Beaumont told CyberScoop. “The one [flaw enabling Stuxnet] from 2010 is 2016’s top exploit still. These [newly leaked tools] share the same hallmarks.”
Although the newest Windows operating systems have patches available to address the vulnerabilities, “unfortunately companies have really long turn-over times for full upgrades on their systems (full OS updates etc… you still see Windows XP out there a lot and Solaris) so I would [definitely] agree with those [predictions],” Henriques explained.
“The life of an exploit doesn’t end with the release of a security patch designed to fix the vulnerability being exploited,” Kaspersky Lab researchers wrote in a blog post last week. “Once made public, a vulnerability can become even more dangerous: grabbed and repurposed by big threat actors within hours.”
Both Stuxnet and the new Shadow Brokers tool came from the same source: The Equation Group, one of the most sophisticated attack groups in the world and widely suspected of being the NSA. Whenever its tools leak to the public, the internet feels the consequences for many years after the fact.