Feds still dragging in DMARC configuration

It’s been more than a month since a mandatory Department of Homeland Security deadline passed for federal agencies to adopt security measures that stop attackers spoofing email — but more than a third have still failed to do so, according to an analysis of public records.
What’s arguably worse is those that have implemented the measure called DMARC — Domain-based Message Authentication, Reporting and Conformance — have in many cases misconfigured it, meaning they remain exposed to spoofing.
Federal IT specialists “aren’t picking up on the issue of subdomains,” explained Ian Breeze, a product manager at Easy Solutions, a vendor that provides software and advice to organizations seeking to implement DMARC, “They’re leaving their email subdomains open to fraud.”
How DMARC works
DMARC works by creating a public record that email systems can check to determine whether a message sender is in fact authorized to transmit on behalf of a particular internet address or domain — like dhs.gov.
Because of the open character of the internet email system, forging a message to look like it comes from dhs.gov is easy to do. It’s a technique widely used by hackers to send messages containing malicious attachments or links. These phishing emails are much more likely to be effective if they appear to come from a trusted correspondent like a government agency.
Having a DMARC record means that a recipient’s email system can check to see whether the address is spoofed. If it is, what happens next depends on how the DMARC record is set up.
Setting the record to “p = none” effectively switches it off, meaning the email will be delivered as usual, but a report will be sent to the domain owner informing them that someone is spoofing their address. It can be set to “p = quarantine,” meaning the email will be delivered to the spam folder of the recipients email. At the highest setting, “p = reject,” the email will be discarded.
‘A large mountain to climb’
It sounds simple, but most large organizations have multiple vendors — like marketing contractors or outsourced human resources services — that send email on their behalf.
“Getting all those third-party contractors together, that what takes the effort,” said Breeze.
“It’s a very large mountain to climb,” he added, noting that ride-hailing company Uber took four months and the help of a contractor to implement DMARC.
And the issue of subdomains — like for instance tsa.dhs.gov or nist.commerce.gov — adds an additional level of difficulty.
“Generally, if you have your DMARC record set to “p=none,” you should have the subdomains set to reject,” he said. If they’re not set “fraudsters can just spoof a fake subdomain [— email.dhs.gov, for example.] … You want to lock down all the infinite possible [fake] subdomains.”
Fortunately, that’s easy — at least in theory. “It’s a 30 second fix,” said Breeze.
But he acknowledged that might not be so simple in the government, where sub-agencies with a seperate CIO office might operate their subdomain independently of the main agency.
Far from perfect
Easy Solutions reviewed public records for 311 .gov domains. As of Feb. 22, 180, or 58 percent, had a DMARC policy. But of those, nearly 30 had set their subdomains policy to none, said Breeze — meaning fraudsters could still spoof a subdomain.
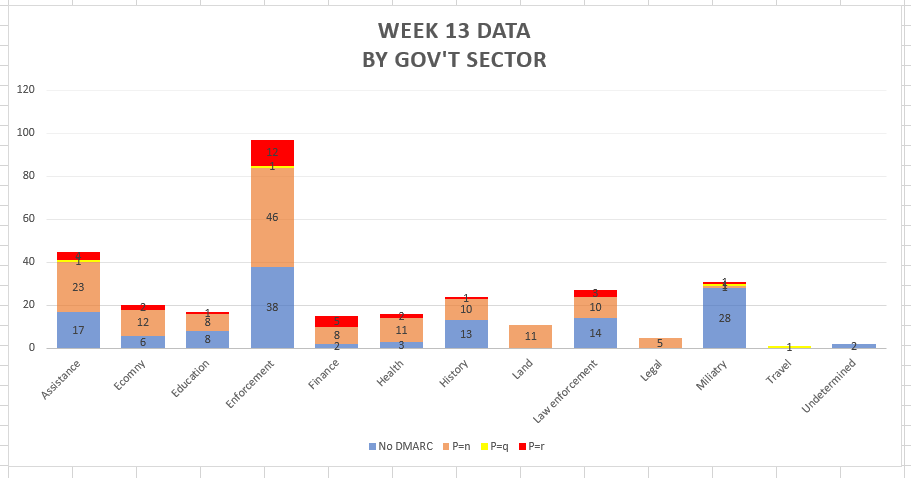
( Source: Easy Solutions)
And 131 domains (42 percent) — including more than 40 law enforcement and defense agencies — still lacked a DMARC record altogether, meaning the agency responsible has blown the mandatory Jan. 15 deadline set by DHS. The Binding Operational Directive the department issued last October gave agencies 90 days to adopt DMARC and a year before they had to switch it to ‘p=reject.’
ValiMail, another email security vendor, has been tracking a much larger dataset of federal domains — 1315 of them. Their numbers show a slightly higher DMARC adoption rate: 831 domains, or 65 percent — although more than 120 were misconfigured in some way.
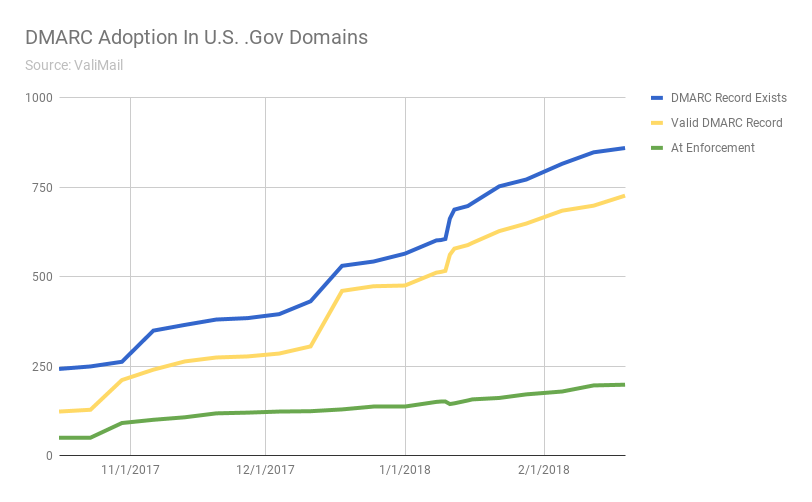
(Source: ValiMail)
A DHS spokesperson disputed both sets of figures, saying “more than two thirds of agencies” had implemented DMARC at ome level — and the vast majority were on track to hit the “p=reject” deadline.
“By the end of October 2018, as required by the BOD, 92 percent of reporting agencies have clear timelines to fully adopt DMARC across their enterprise,” the spokesperson told CyberScoop.
The spokesperson didn’t address what would happen to agencies that were dragging their feet.
“DHS continues to work with these agencies to resolve identified challenges impacting the implementation timelines and address concerns related to vendor constraints, acquisition lifecycles, and potential impacts to mission-critical systems,” the spokesperson said.
Former DHS official Phil Reitinger said department officials were “in the best position to decide if the non-compliant agencies are facing real barriers or dragging their feet.”
But he added there needed to be consequences for agencies that are lagging behind, noting that President Donald Trump’s cybersecurity executive order last year promised “Agency heads will be held accountable by the president.”



