China’s national vulnerability database is merely a tool for its intelligence agencies

China’s National Vulnerability Database is being manipulated so vulnerabilities used by Chinese-linked hacking groups can be taken advantage of, according to new research from Boston-based cybersecurity firm Recorded Future.
The database (CNNVD) is on average two times faster in posting vulnerabilities, and it is significantly more comprehensive than its U.S. counterpart, but researchers showed in November that China’s intelligence community effectively runs the database. The Ministry of State Security (MSS), where the CNNVD is housed, evaluates vulnerabilities before they are published to see if they can be used in intelligence operations.
Now, Chinese officials are doctoring initial vulnerability publication dates in what appears to be a sloppy cover-up, researchers say.
“CNNVD had gone back and backdated the publication days for 99 percent of the vulnerabilities we identified,” said Priscilla Moriuchi, the director of strategic threat development at Recorded Future. “What they had done is eliminate the publication lag which is one of the things we used to determine which of the vulnerabilities the MSS is interested in.”
The research shows that countries known for advanced hacking operations continually go to great lengths to obfuscate their tools, techniques and procedures.
Below is an image illustrating the issue: On the left, a screenshot from October 23, 2017 shows vulnerabilities found in software from the Chinese firm Adups. This software has repeatedly been found to secretly siphon off large quantities of user data. The publication date is September 6, 2017. On the right, the same page with the publication date changed to January 13, 2017, a backdating of 236 days.
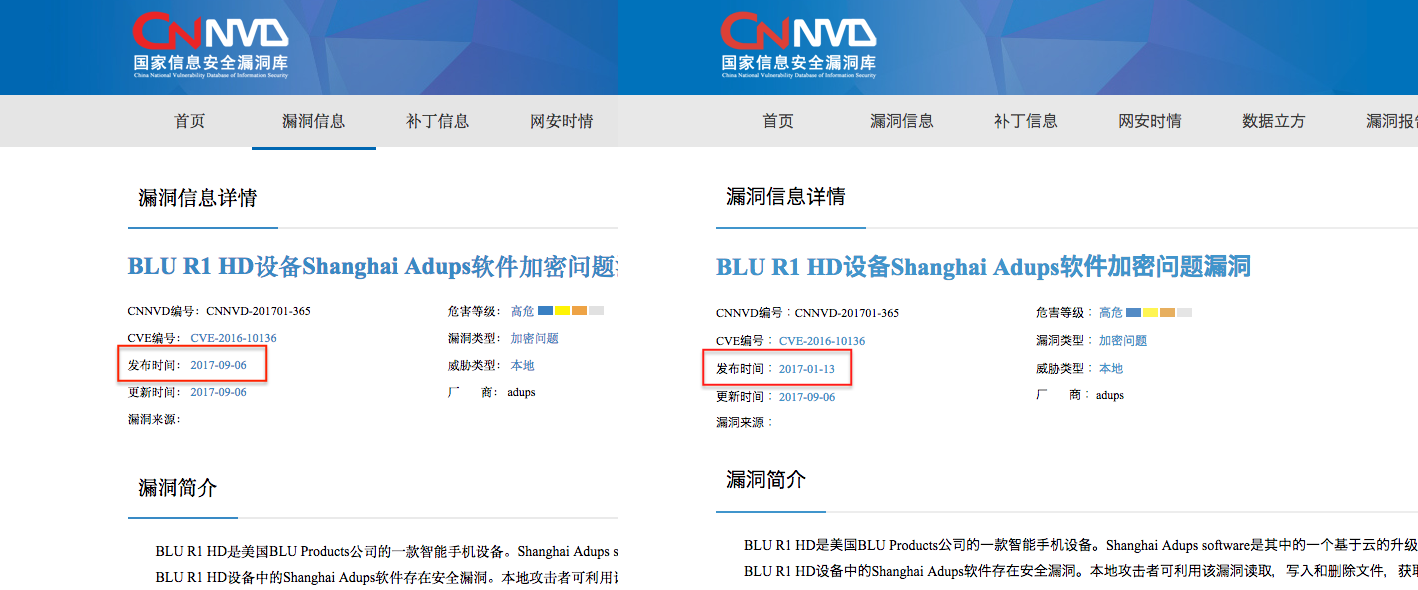
(Recorded Future)
Moriuchi and co-researcher Bill Ladd said that by retroactively changing the original publication dates on these statistical outliers, “CNNVD tried to obfuscate which vulnerabilities the MSS may be utilizing and limit the methods researchers can use to anticipate Chinese APT behavior.”
“It is not surprising that the Chinese government is holding on to a small number of high-value vulnerabilities that it is using to penetrate targets to further national security goals,” Paul Triolo, practice head for geo-technology at the Eurasia Group, told CyberScoop in November.
The delays in CNNVD publishing have an impact in the greater digital ecosystem. Last year, publication of the Microsoft Office vulnerability CVE-2017-0199 came out 57 days late on the Chinese database. In the meantime, a Chinese advanced persistent threat group exploited the vulnerability in cyber operations against Russian and Central Asian financial firms.
CNNVD is primarily used by East Asian companies. MSS’s primary mandate is domestic surveillance. Its secondary mandate is foreign intelligence. Controlling CNNVD allows them to control the information environment in China, Moriuchi explained.
“This data manipulation reinforces the dominance of the secrecy mandate over transparency in China,” Moriuchi and Lund wrote. “Instead of taking steps to remove the undue influence of secrecy and the intelligence services over vulnerability reporting, CNNVD has gone the opposite way and sought instead to further conceal that influence.”
CNNVD officials did not respond to a request for comment.
Editor’s note: Join us on April 16 for SF CyberTalks to hear Priscilla Moriuchi and a number of other cybersecurity experts discuss priorities, trends, innovations, and ways to tackle unprecedented security challenges.



