Stolen U.S. drone documents found for sale on dark web

Sensitive U.S. military drone blueprints and training documents were recently posted for sale on the dark web, according to Boston-based data analytics and intelligence firm Recorded Future.
Analysts with Recorded Future say the stolen drone documents appear to be legitimate, having come from an airman who is currently stationed at a Nevada-based U.S. Air Force facility. The information was apparently breached through a known, outdated router vulnerability that affects a product made by computer networking company NetGear.
The stolen documents include the names of active Air Force personnel in addition to other technical information, Recorded Future said. Leaks containing such information — about people involved in a specific military unit — would typically be considered a counterintelligence threat.
The drone blueprints provided unclassified yet sensitive information about the MQ-9 Reaper, a drone that is currently used for both surveillance and armed combat operations by the U.S. and its allies. The MQ-9 was originally developed by defense contractor General Atomics.

Image provided by Recorded Future
The disclosure highlights the risks posed to systems that store technology manuals, schematics and other military documents which hold value to foreign governments, black market dealers and others.
The FBI and Defense Department’s CIO office did not respond to a request for comment about Recorded Future’s findings. The hacker responsible is also believed to be in possession of Pentagon material related to an improvised explosive device (IED) briefing.
A blog posted Wednesday by Recorded Future reads: “[On June 1,] an English-speaking hacker claimed to have access to export-controlled documents pertaining to the MQ-9 Reaper unmanned aerial vehicle (UAV). Insikt analysts engaged the hacker and confirmed the validity of the compromised documents. Insikt Group identified the name and country of residence of an actor associated with a group we believe to be responsible.”
Recorded Future say it has been working closely with law enforcement to provide evidence of the breach. The company is largely staffed by former U.S. law enforcement and intelligence professionals and is backed by the CIA’s venture capital investment arm.
While Recorded Future declined to name the user or the forum where the blueprints were posted, analysts have documented several of the hacker’s conversations. In one exchange, the hacker claimed to have access to live, in-flight footage shot from a drone that may still be operated by a government agency. That claim, which would suggest the hacker had wide access to a possibly classified network, could not be verified by analysts.
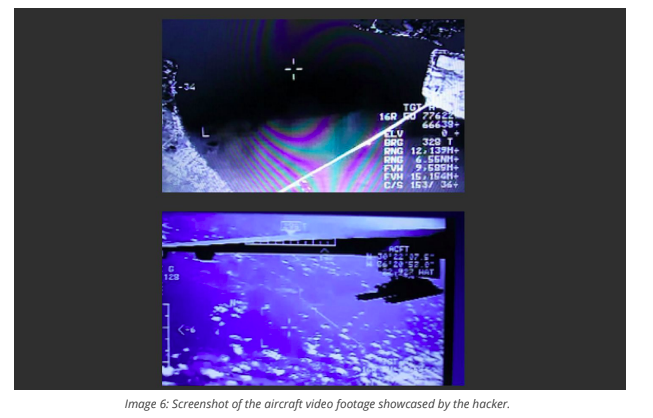
Image provided by RecordedFuture
Others have been interested in stealing secrets about General Atomics’ technology for years.
In February, an Associated Press investigation found that Russian-linked hackers had heavily targeted employees of General Atomics since at least March 2015 with specially tailored phishing emails. The hackers were believed to be associated with a group known as “Fancy Bear” or “APT28,” which may be best known for breaching the Democratic National Committee in the run up to the 2016 U.S. presidential election.



